1. Introduction
In this tutorial, we’ll discuss the encryption algorithms in brief. We’ll discuss one-way encryption, symmetric encryption and public key cryptography.
2. One-way encryption
These algorithms are also known as hashing algorithms. A one-way algorithm takes an input string and generate an output known as the message digest. The output can not be converted back to the original string. This is why this technique is referred to as one-way encryption.
For example, the requesting client sends the encrypted data to the server. The server can apply the same hash function on the original stored information and compare the incoming hash with the generated hash to check if both are same.
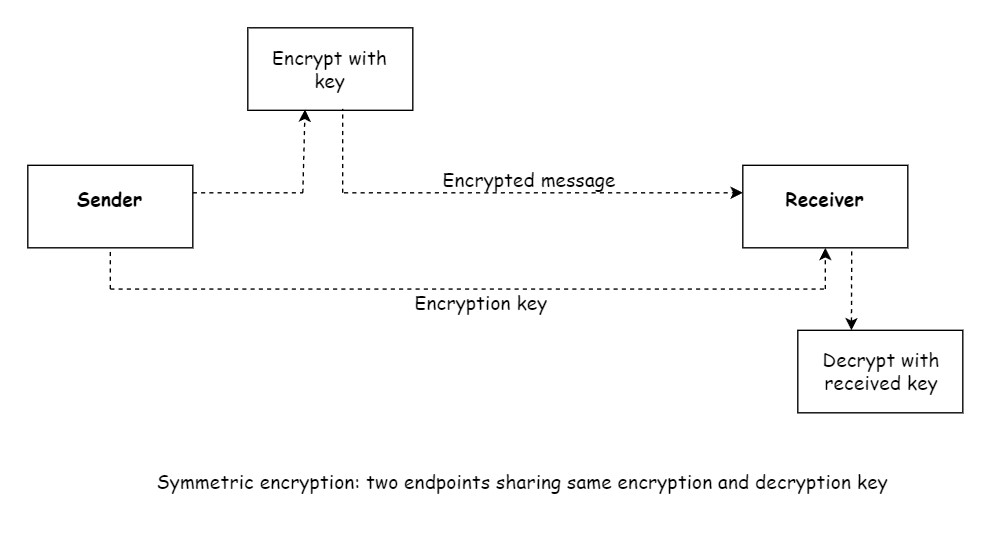
3. Symmetric encryption
These algorithms provide two functions for encryption and decryption. A string can be converted into an encrypted form and then can be converted back to the original string. In this technique, the sender and receiver share the same keys for encryption and decryption. The problem with this approach is how to share the key between the endpoints of the communication. A common approach is to use a parallel secure channel to send the keys.
Symmetric encryption is commonly used for securing large amounts of data, such as file encryption or secure communication between two parties who already share a secret key.
- Key: Symmetric encryption uses a single shared secret key for encryption and decryption. This means that both the sender and the recipient use the same key.
- Speed: Symmetric encryption algorithms are generally faster and more efficient than asymmetric encryption algorithms.
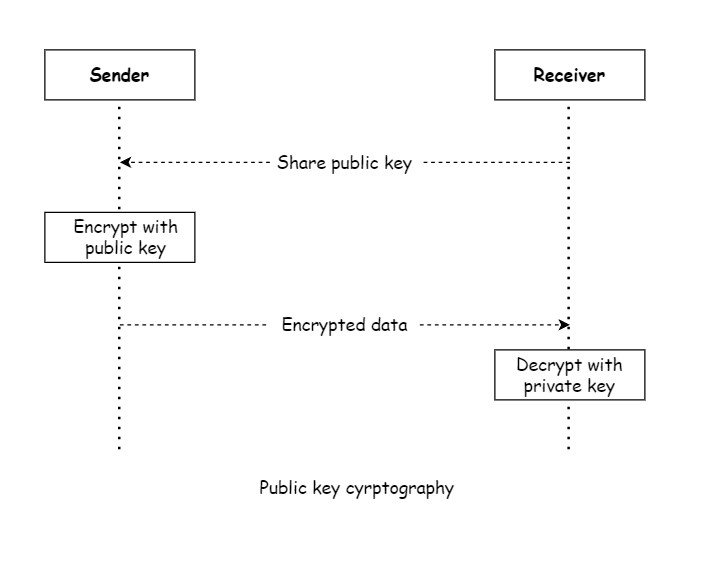
4. Public key cryptography
This technique is based on asymmetric cyrptography. In this technique, the key used for encryption is different from the key used for decryption. The key used for encryption is known as public key and the key used for decryption is known as private key.
The public key is freely available to anyone, while the owner keeps the private key secret. Asymmetric encryption provides a higher level of security because the private key is not shared or transmitted. Asymmetric encryption is often used for secure key exchange, digital signatures, and secure communication between parties who do not have a pre-shared secret key.
The advantage of this approach over symmetric key encryption is that we need not to share the decryption key, so only the intended receiver of the information can decrypt the message. Following the normal scenario:
- The intended recipient shares her public key with anyone who wants to send her information.
- A sender encrypts the information with the receiver’s public key and sends the message.
- The receiver uses her private key to decrypt the message.
- No one else can decrypt the message because they don’t have the receiver’s private key.
5. Conclusion
In this short tutorial, we discussed the encryption algorithms in brief.
